distributed
一些密码/逆向
re
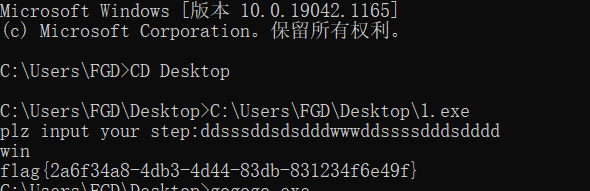
re1.exe
迷宫题,把迷宫爬出来
1 | ******************** |
得到通路为
ddsssddsdsdddwwwddssssdddsdddd
re1.pyc
直接丢进在线工具里
https://tool.lu/pyc
1 | #!/usr/bin/env python |
逆向脚本
1 | from base64 import * |
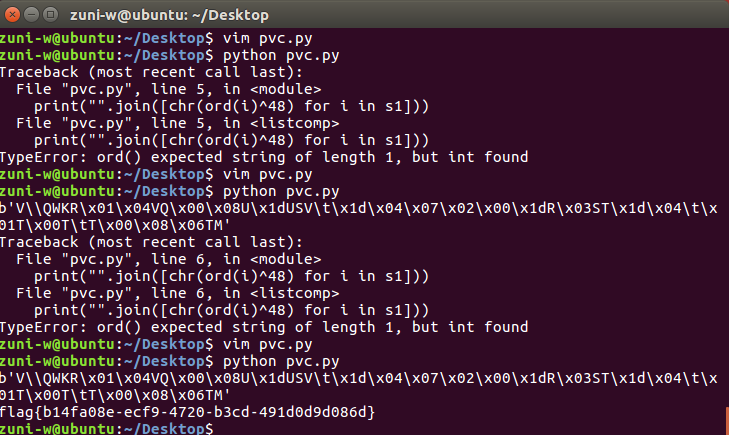
re10
寻址表,直接复制粘贴脚本
1 |
|
gogogo
读出来是华容道,右%上@下#左$
然后手写了一会儿,zuobudongle
写了一个笨笨的bfs
1 | from copy import * |
跑了跑,失败
然后找到了一些开源的华容道项目https://github.com/Dpxx/Klotski-15puzzles
然后有个开源https://dpxx.github.io/

###\(@%#\)\(@@@%#%#%@\)@%##$$@@%##%#
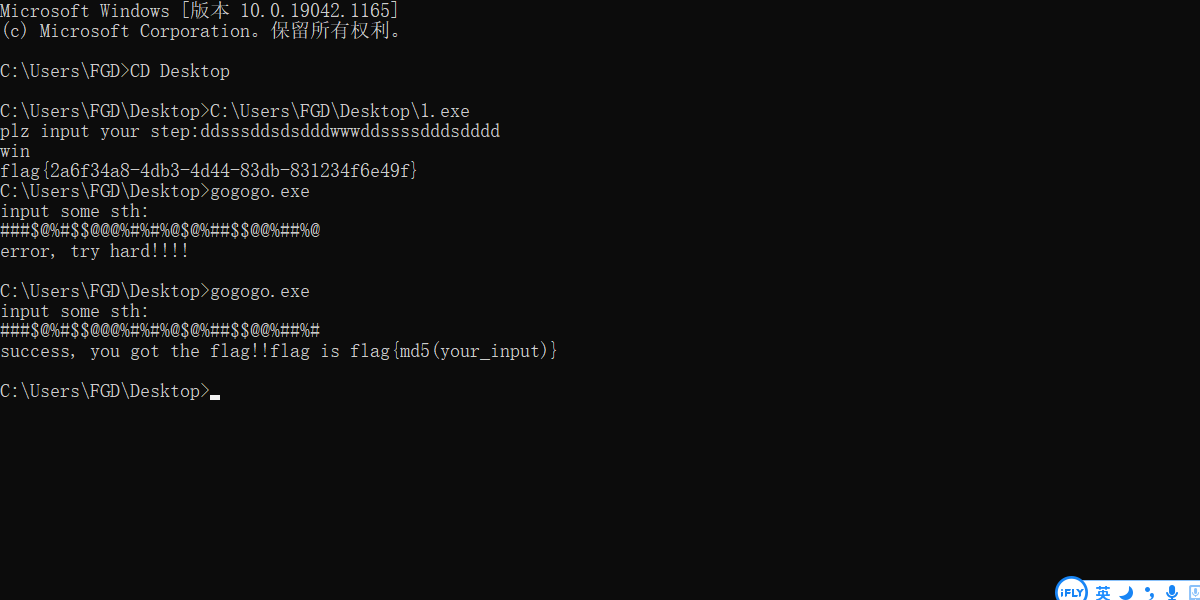
re12
aspack壳,直接一路运行到input,然后去搜关键字符串找到了代码段。
复制粘贴略加修改得到
1 | #include<cstdio> |
得到结果
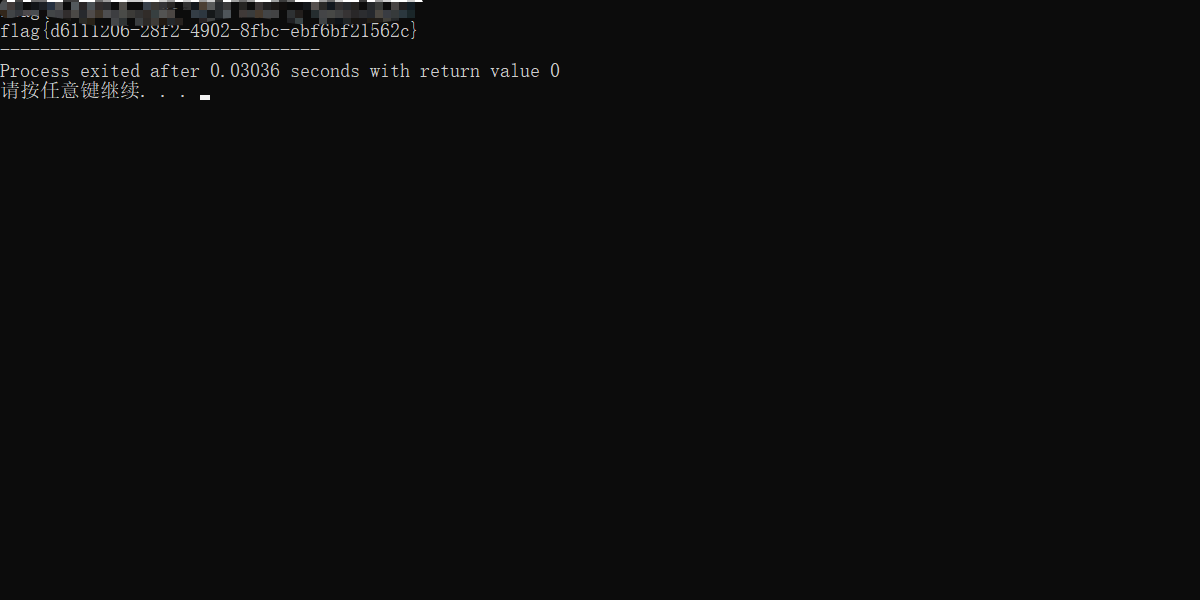
cry
rsa padding attack
coppersmith,构造最大公因式。

(感谢这个题,顺带切了cryptohack)