ciscn_2021 HASH-TEAM RE/cry WP
以下为本次赛中的WP
re-glass
流程
发现是apk,直奔lib的.so文件
然后ida打开,发现字符长度39,接着发现最后的内存比较长度也是39,应该没有改变长度的操作。
把比较的内存dump下来。
在输入后发现重要字符串“12345678”,猜测是密钥。
然后依次点进去三个函数,前两个是rc4,没有魔改的。
第三个函数先划分成三元组,并通过异或加密,最后再跟密钥异或加密。
由于后两步使用ida python直接写的脚本,在此重补。
第一步
dump+异或
1 | s='''A3 1A E3 69 2F BB 1A 84 65 C2 AD AD 9E 96 05 02 1F 8E 36 4F |
第二步
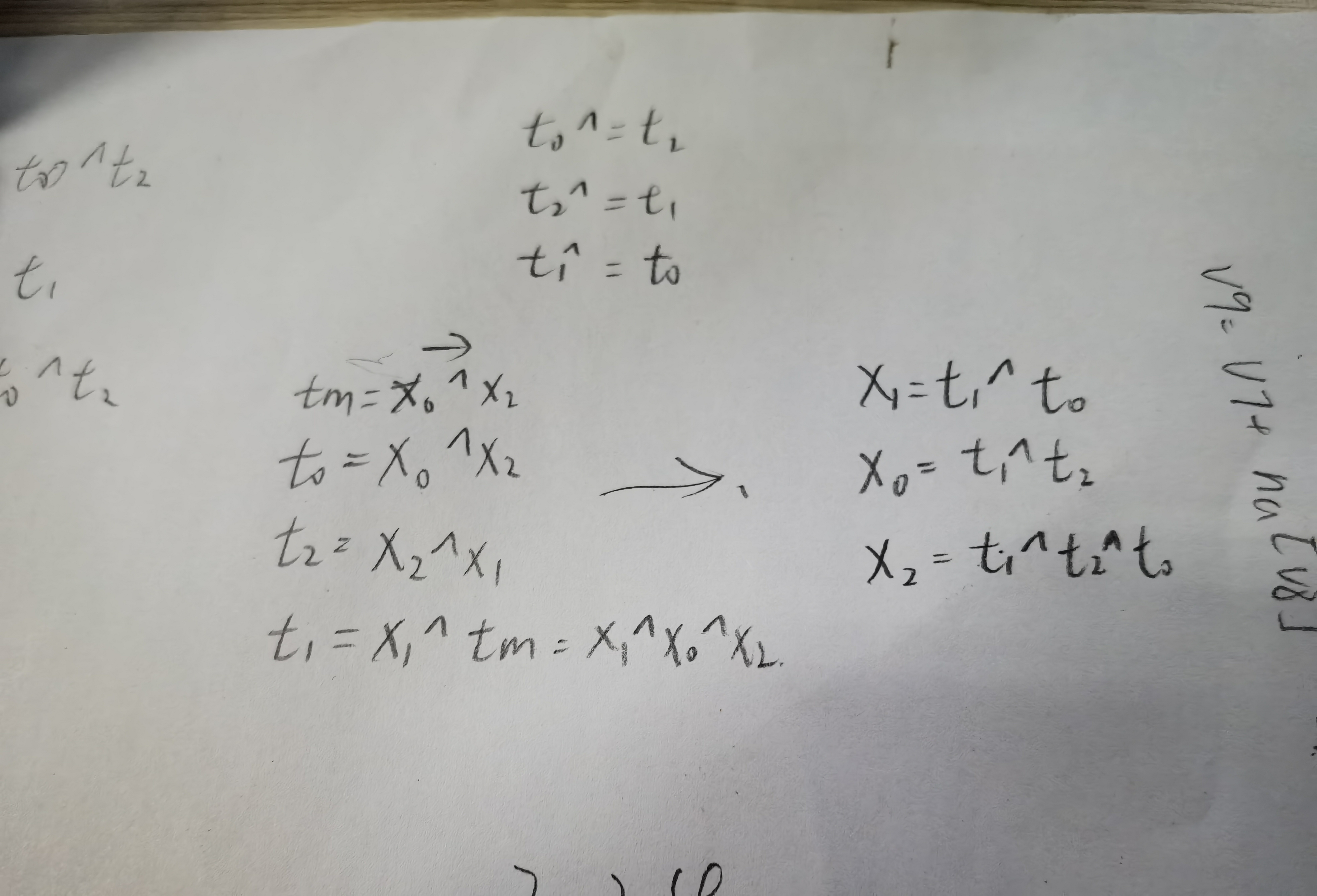
写脚本
1 | s2=[0]*39 |
第三步
直接用之前的脚本
1 | import requests |
re-baby.bc
流程
查资料可知这是个llvm,下载llvm工具链和clang
1 | llvm-dis baby.bc |
然后分析out文件
输入长度25,且只有\(['0','5']\)可输入,后边的判断明显是5个一组,大胆猜测是5x5的结构,创建结构体。
第一个fill函数的逻辑是对于已经有值的格子判断输入为0,对于无值的格子则存入。
第二个函数docheck()函数首先进行了行列查重,然后按照比较结构体是1还是2约束大小。
其实就是个数独。
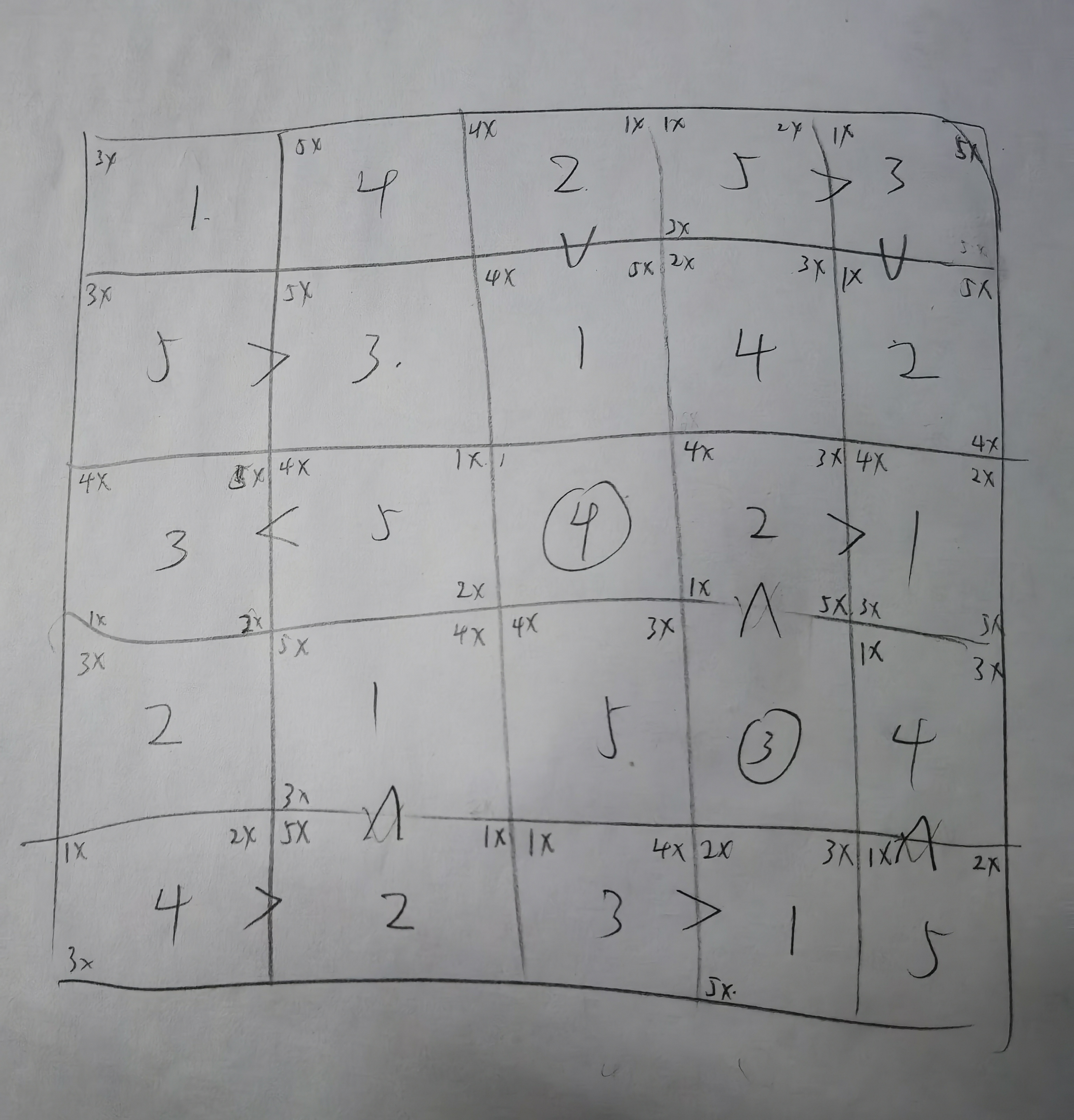
尝试输入
ps:本题有可能出现非预期的含有0的解,但未测试。
cry-rsa
发现是分成了三段。(这个题在终端写的)
第一段低指数加密攻击,直接开方得到。
1 | from gmpy2 import * |
第二段是中国剩余定理,直接对17和65537剩余定理可得。
1 | gcdext(17,65537) |
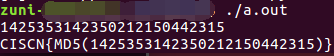
发现是西风颂,第三段不会做,直接爆破原文。
1 | from Crypto.Util.number import long_to_bytes,bytes_to_long,getPrime |
然后从hashlib取md5结束。